Enterprise Campus Network
As already discussed, there are four Major functional Module in Enterprise Campus Network
1. Campus Infrastructure Module
- Building Access
- Building Distribution
- Campus Backbone(Core)
2. Network Management Module
3. Server Farm Module
4. Edge Distribution Module
Key requirement for Enterprise Campus Network.
Our Enterprise Campus Network must maintain certain level of each one of these.
Functionality: Network should fuction properly as per expectation.
Performance: Network should have a constant performance and stable throughput.
Scalability:We all want our network to grow.Network should have such scalability (Physically and logically)
Availability:Network should have redundant connection to make it available all the time.
Manageability:Network should be manageable instantly from a single point
Cost Effectiveness:Keeping the cost minimum.
Cisco's Network Designer's have developed a methodology a seven steps process when designing a enterprise campus network. It is based on years of experience from designers.
1. Determine application and data requirement
- Need to identify which application will be running at user end
- What would be the bandwidth requirements
2. Design the logical Network
3. Design the physical network
- Determine where to place layer 2 and layer 3 devices
- STP, transmission media (copper or fiber)
4. Select specific Cisco network devices at each location and create topology diagrams
- Select specific network devices, type of routers,type of modems/switches, FWs, IDS
5. Select an IP addressing strategy and numbering scheme
- IPv4, IP v6, sub-netting, summarization,
6. Select a routing protocols
- Based on performance, scalability and availability
7. Design the Edge Distribution Module
- How to we send and receive data from Enterprise Campus Module
CISCO NSF with SSO
Cisco NSF (Non Stop Forwarding) with SSO (Stateful switch-over)
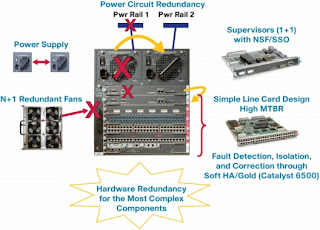
Cisco Nonstop Forwarding (NSF – also known as Graceful Restart) with Stateful Switchover (SSO) is a Cisco innovation for platforms with dual route processors (Cisco 7304, 7500, ASR1000, 4500, 6500, 7600, 10000, 12000 and CRS), allowing a NSF Capable router which has experienced a hardware or software failure of an active route processor, to maintain data link layer connections and continue forwarding packets during the switchover to the Standby route processor.
Nonstop Forwarding works with the Stateful Switchover (SSO) feature in Cisco IOS software. NSF works with SSO to minimize the amount of time a network is unavailable to its users following a switch-over. The main objective of Cisco NSF is to continue forwarding IP packets following a Route Processor (RP) switchover. It maintains and updates Layer 3 routing and forwarding information in the backup route processor. This ensures that the forwarding of IP packets and routing protocol information are continuous during the switchover and route convergence process. It eliminates router downtime, and increases network availability during scheduled maintenance of a route processor, or a route processor failure.
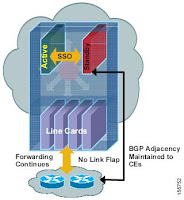
A Cisco router equipped with dual route processors can maintain Layer 2 data link connections and up-to-date “next-hop” information (FIB and Adjacency tables) to continue forwarding packets in the event of a route processor switchover until the routing protocols recover – In other words each protocol depends on CEF to continue forwarding packets during switchover while the routing protocols rebuild the Routing Information Base (RIB) tables. Once the routing protocols have converged, CEF updates the FIB table and removes stale route entries. CEF then updates the line cards with the new FIB information.
During switchover, system control and routing protocol execution is transferred from the active processor to the standby processor. The time required by the device to switch over from the active to the standby processor ranges from just a few seconds to approximately 30 seconds, depending on the platform.SSO is a prerequisite for NSF.
NSF can be used to improve network performance in a totally different way than traditional convergence, it Simply stops the reporting of neighbor failure, avoiding the need of re-convergence in the first place, while keep forwarding the packets until the neighbor resets its control plane. Using NSF you can virtually reduce network convergence to zero in case of control plane failures, but this implies the need for routers participating in this operation to be either NSF capable or aware, plus another critical implication which is that the failure must be recovered within the hold down timer limit of the protocol NSF/SSO benefit is not just nonstop forwarding, but also reducing route flaps, which is a significant factor in large scale networks, since route flapping results in all network routers converging after each route flaps, but with NSF/SSO no route flapping is reported – Since the NSF capable router(s) peers don’t report the NSF capable neighbor down to the rest of the network.
Objective
- Avoid TCP session to be interrupted
- User SSO in Layer 2 environment
- Use NSF with SSO at Layer 3.
- Reduce outages to 1-2 seconds avoiding single point of failure
- Supported by all cisco devices and routing protocols such as EIGRP, OSPF, BGP, ISIS etc
- Not supported on OSPF virtual links, HSRP does not work with NSF.
- From the CCIE SP Lab perspective it is only supported on the 7200 router on the lab equipment list.
Configuration Example: [For OSPF]
Router# show cef state <- Verifies that router is NSF capable
Router# configure terminal
Router(config)# router ospf 300
Router(config-router)# nsf
Router(config-router)# exit
Router# show running-config <- Verifies NSF for OSPF
!
router ospf 300
log-adjacency-changes
nsf <------- nsf is used with OSPF
network 192.168.10.0 0.0.0.255 area 0
network 192.168.20.0 0.0.0.255 area 1
network 192.168.30.0 0.0.0.255 area 2
Cisco IOS Software Modularity
1. Operational consistency
2. Memory Protection
3. Fault containment
4. Process restart- ability (process can be start individually)
- Command is Process restart <process> should be use with caution
5. Process Modularization (every process is different from other process)
6. Subsystem ISSUs (In service software upgrade)
- A Selective system maintenance -during runtime
- Versioning and patch management functionality
Benefits
- Minimize unplanned downtime
- Software up-gradation is simple
- Modularity is maintained
Control Plane
- EEM (Embedded Event Manager)-CPU utilization, SNMP, Syslog,counters
- Routing Protocol
- Multicasting protocol-PIM,IGMP
Data Plane
Management Plane










